As a fan of Freenet due to its decentralization and anonymity and an user of Qubes OS, I wanted to combine these two to achieve better security. Specifically, my goal is to make it work like Whonix, splitting it into a “Freenet Gateway” and “Freenet Workstation”, with the latter not being able to connect to other places except the gateway.
Steps
- Create a firewallVm as the gateway, with the Freenet software installed on it.
- Create an appVm that uses the gateway as its firewallVm. This will act as the workstation.
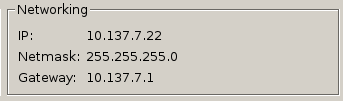
- Right click the workstation entry in the VM manager, click “VM Settings”, and take note of the “IP” and “Gateway” address. These will be referred to as
[IP] and [GATEWAY] respectively in the following steps.
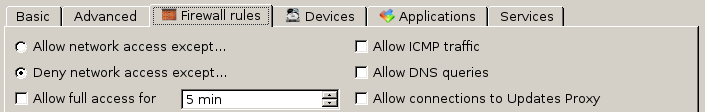
- Navigate to the “Firewall rules” tab in the workstation settings, choose “Deny network access except…”, and untick all three boxes on the right.
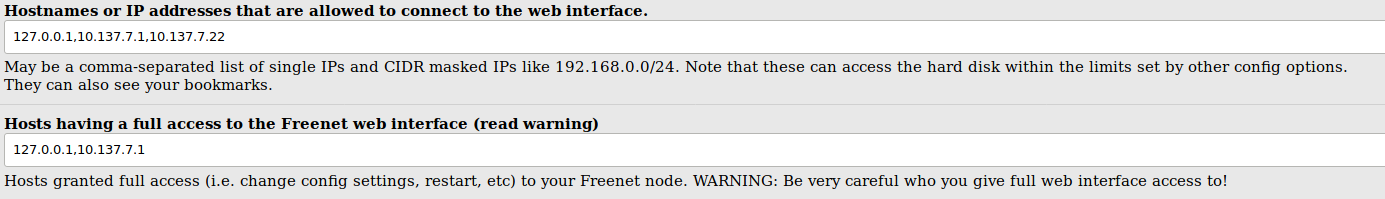
- In the webUI of Freenet (on the gateway), navigate to “Configuration -> Web Interface”
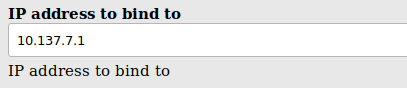
- Change “IP address to bind to” to
[GATEWAY]
- Change “Hostnames or IP addresses that are allowed to connect to the web interface” to
127.0.0.1,[IP],[GATEWAY].
- Change “Hosts having a full access to the Freenet web interface” to
127.0.0.1,[GATEWAY].
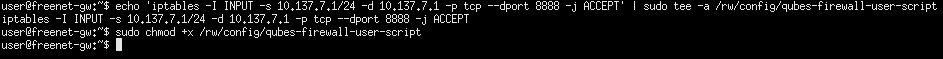
- In the gateway, run the following commands:
echo 'iptables -I INPUT -s [GATEWAY0]/24 -d [GATEWAY] -p tcp --dport 8888 -j ACCEPT' | sudo tee -a /rw/config/qubes-firewall-user-script
sudo chmod +x /rw/config/qubes-firewall-user-script
- Reboot the gateway
This way, Freenet can be accessed in the workstation VM at http://[GATEWAY]:8888/.
Also, note that, due to how networking in Qubes works, you may have to start the workstation VM before launching Freenet on the gateway.